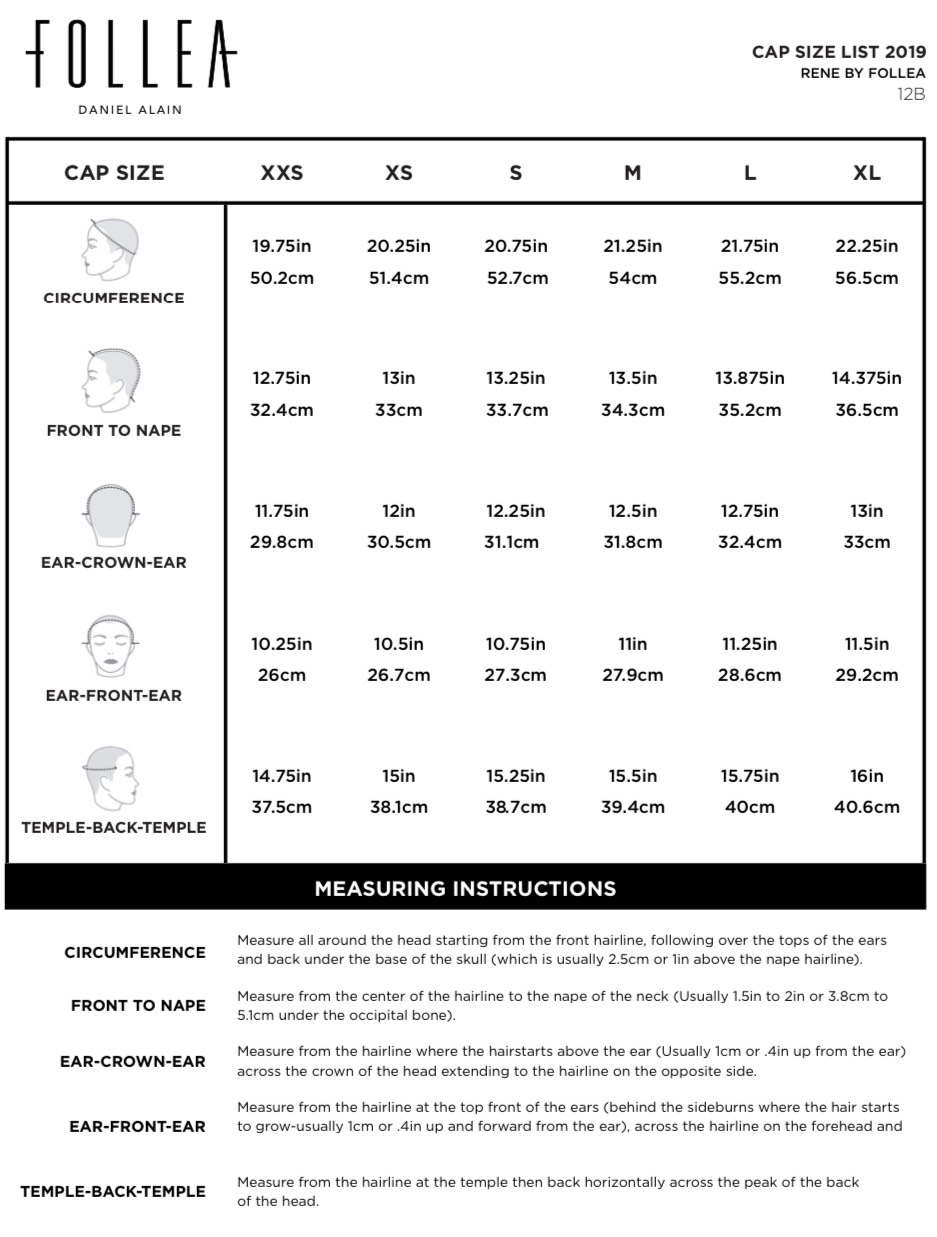
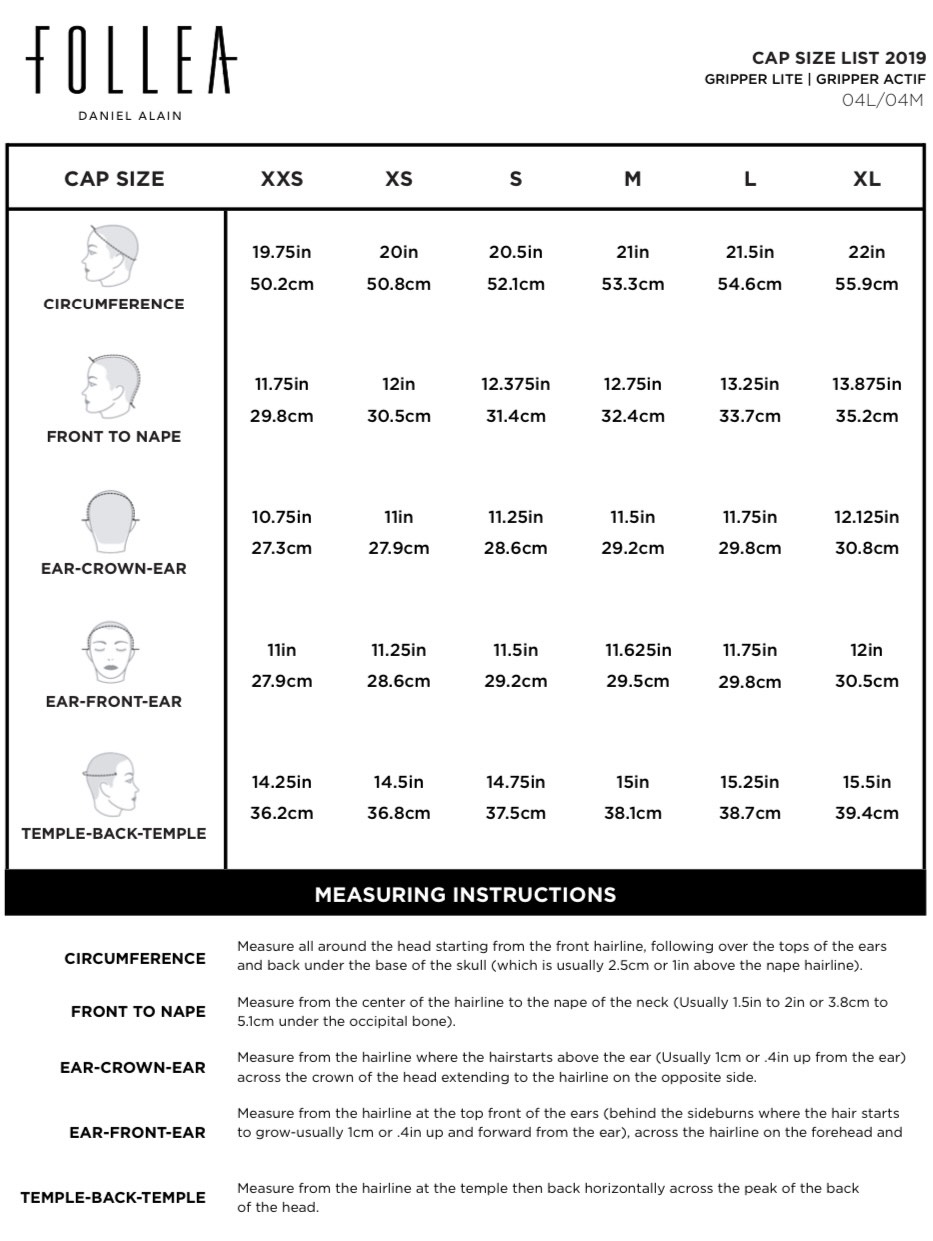
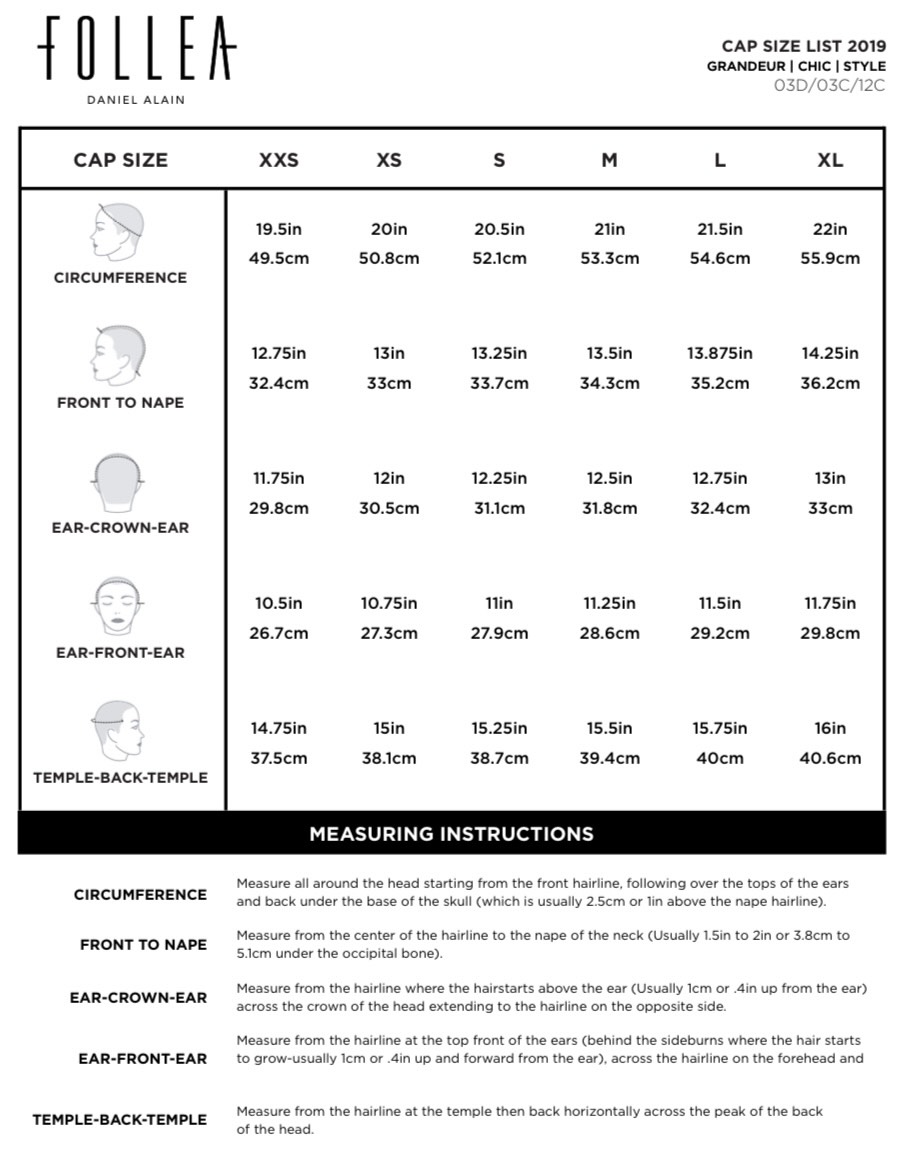
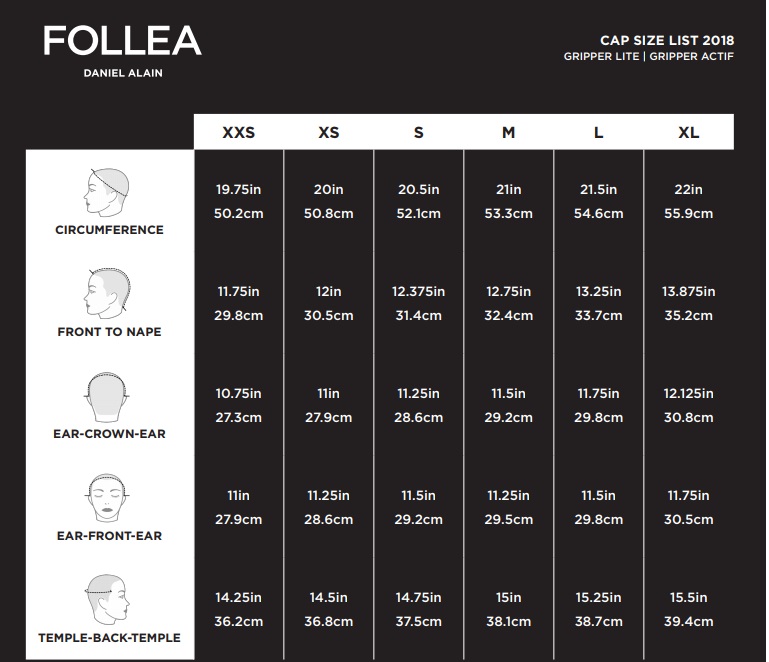
Ensure that double quotes are not used in any of the GSK8 directories specified and confirm the DLLs do in fact exist in the path directory that was defined. Please try again later or use one of the other support options on this page. Did you search for an IBM acquired or sold product ? If so, follow the appropriate link below to find the content you need. Again, you want to be running command prompt as an administrator in an elevated mode. The following examples show how to use the run-time loading and linking facilities using language-specific Windows API bindings. The following examples show how to use language-specific bindings to import symbols for linking against a DLL at compile-time.
I don’t see any reason MS would want you to casually tamper with registry. So it might be a reluctance on their part to change it in favor of experience as well. The names for products or features are usually determined long after the code is written. Tweaking the Windows Registry to disable the ‘hidden’ administrator account as well as restricting access to specific programs ensures beefed-up security. Making changes in the Windows Control Panel results in the same thing – the changes made are actually done in the Registry. Like I said, there are a few more registry keys that are likely to be targeted by malware authors and adversaries.
Options For Real-World Systems For Missing Dll Files
The recent files in File Explorer make it easy to access them quickly. However, at times Windows users need to clear their recent files and start afresh. In addition, some rocketdrivers.com/dll/chakra_dll users also need to clear their traces before anyone else uses the same PC. Therefore, windows also allow you to disable recent files in the Quick access area. JumpList Editor is potentially lavasofttcpservice.dll more useful because it has the ability to include standard or frequent lists into your own custom Jump Lists. This makes them behave much more like what you get from real Jump Lists. Select a pinned icon or opened window to create a list for, and then edit the list to your requirement.
- The typical desktop PC or laptop has many pre-installed apps, including word processing tools and internet browsers.
- Then, run the program and follow the on-screen instructions.
- In the next dialog you must enter a name for the registry file you loaded.
- To disable for one app, make that Jump List file read only after it’s newly created and cleared.
Inside the Registry, the settings themselves are stored in a few different formats. The most common is the DWORD a “double word”, which is jargon for a 32-bit number but the Registry can also store binary code, text strings and various other types of data. If you look in the right-hand pane of the Registry Editor, you’ll see the “Type” column shows what sort of data each value is. The Registry isn’t really designed for users to tinker with. When the likes of you and me want to configure our Windows settings, we’re expected to use the friendly graphical interfaces built into Windows, such as the PC Settings app or the Device Manager. These bits of software then access and update the Registry behind the scenes.
An Analysis Of Dll Solutions
Programs can’t be launched from Start Search results. Resetting the Cortana data folder as in Fix #3 above also fixes a problem where when you search for a program via the Start menu, programs don’t start when launched from Cortana Search results. Refer to the Reddit thread Windows 10 Search Bar won’t open programs that are not listed as “Trusted Windows Store App where many … The attacker made everything from inside the SQL Server service without actually having access to the OS, but still had a deep impact on the underlying OS configuration. Run and RunOnce registry keys cause programs to run each time that a user logs on. The registry checker tool backs up the registry, by default, to %Windir%\Sysbckup Scanreg.exe can also run from MS-DOS. Through PowerShell scripts files, an administrator can prepare scripts which, when executed, make changes to the registry.